Cybersecurity for Medical Devices in a Connected Healthcare System
By Alex Wilson and Andreas Rollman
EXECUTIVE SUMMARY
The drive toward digital business transformation that enables a digital healthcare system, with all of the benefits of shared healthcare data, is inevitable. This requires both medical device manufacturers and end users to consider the new concerns of cybersecurity, in order to meet regulatory requirements and mitigate risk for their company brand and reputation.
This is no longer a “nice to have” device feature. Cybersecurity response must be incorporated into the entire device lifecycle — not only in the design but also in development, manufacturing, operational maintenance and decommissioning, and how the device will operate in an IEC 80001 conformant healthcare environment. This becomes a crucial part of device manufacturers’ success in operating against both existing and new competition.
Wind River® works with medical device manufacturers to ensure usage of the latest best practices. By properly designing security into medical devices, manufacturers can avoid financial damage, reputational damage, and potential risk to human lives.
MEDICAL DEVICES AND REGULATIONS
Device manufacturers used to have the luxury of stipulating that their devices would be deployed only on a network secured behind a firewall. Recent thinking has become more realistic, accepting that not every hospital network that is supposed to be secure truly is secure in practice. IT staff in hospitals, just as in other industries, struggle to keep their networks patched and up to date. Increasingly, they are asked to connect greater numbers and more diverse types of devices to that network, and now to cloud-based services outside of the hospital, resulting in many exceptions to the original rules of deployment. In fact, recent evidence suggests that even being behind the firewall no longer means being in a safe haven3 from a security perspective, with rogue devices and poor security procedures in place in many establishments. Medical devices are also being deployed beyond the hospital walls in long-term care facilities or in the home, where there are no IT departments to build a security process and a secure network.
The Food and Drug Administration is taking cybersecurity seriously, and the guidance from October 2014, “Content of Premarket Submissions for Management of Cybersecurity in Medical Devices,”4 was the first step. This publication recommended that, prior to market submission, manufacturers consider security aspects of their devices, including:
- Identification of assets, threats, and vulnerabilities
- Assessment of the impact of threats and vulnerabilities on device functionality and end users/patients
- Assessment of the likelihood of a threat and of a vulnerability being exploited
- Determination of risk levels and suitable mitigation strategies
- Assessment of residual risk and risk acceptance criteria
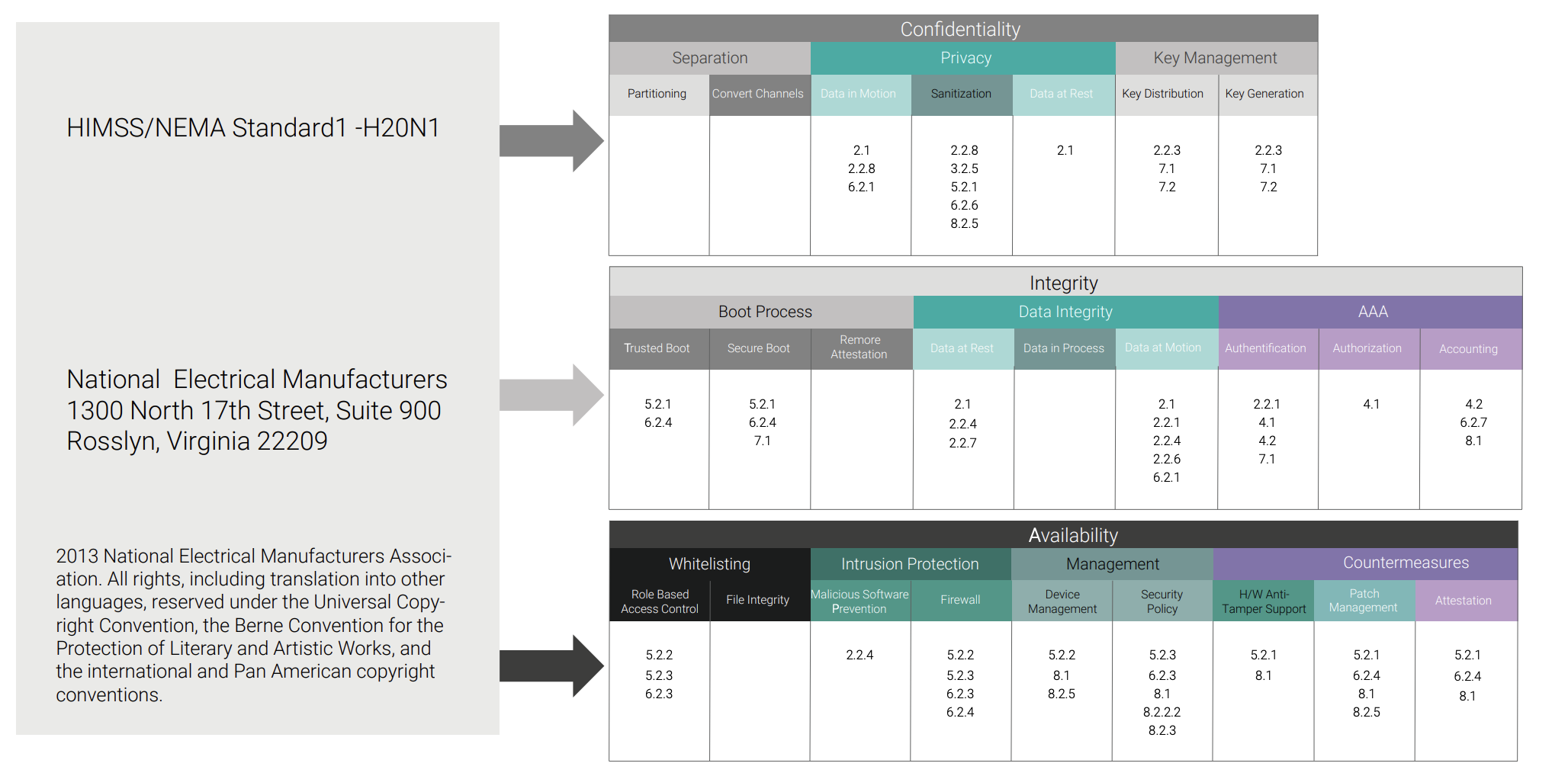
Of note, the guidance recognized several well-known security standards that could be used to achieve this goal, including IEC 80001 and IEC 62443. The recognition of the standards is a good start, but applying them to healthcare devices and infrastructure requires more knowledge and expertise.
Let’s take IEC 80001, for example. From the IEC website: “IEC 80001-1:2010 applies after a medical device has been acquired by a responsible organization and is a candidate for incorporation into an IT-network. It applies throughout the lifecycle of IT-networks incorporating medical devices. IEC 80001-1:2010 applies where there is no single medical device manufacturer assuming responsibility for addressing the key properties of the IT-network incorporating a medical device. IEC 80001-1:2010 applies to responsible organizations, medical device manufacturers and providers of other information technology for the purpose of risk management of an IT-network incorporating medical devices as specified by the responsible organization.”
So what does this mean? For the medical device manufacturer, this does not apply to an individual device independently but rather to how their device supports and is incorporated into a connected healthcare system that is supporting IEC 80001. So an RFQ that says, “How does your medical device conform to IEC 80001?” may not immediately make sense, but what they are asking is how one operates the device in an IEC 80001 conformant environment
Conversely, IEC 62443 covers many aspects of industrial control systems but is not specific to medical devices. So you need to understand how to apply it, and how it can assist you in applying a security strategy that meets the end user requirements in order to incorporate your device into an ISO 80001–based healthcare system.
The FDA guidance was also augmented in December 2016 with “Postmarket Management of Cybersecurity in Medical Devices,”5 which addresses cybersecurity risk management for deployed devices. This guidance states, “Cybersecurity risk management programs should emphasize addressing vulnerabilities which may permit the unauthorized access, modification, misuse or denial of use, or the unauthorized use of information that is stored, accessed, or transferred from a medical device to an external recipient, and may result in patient harm. Manufacturers should respond in a timely fashion to address identified vulnerabilities.”
The postmarket guidance also states, “Effective cybersecurity risk management is intended to reduce the risk to patients by decreasing the likelihood that device functionality is intentionally or unintentionally compromised by inadequate cybersecurity. An effective cybersecurity risk management program should incorporate both premarket and postmarket lifecycle phases and address cybersecurity from medical device conception to obsolescence. It is recommended that manufacturers apply the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity.”
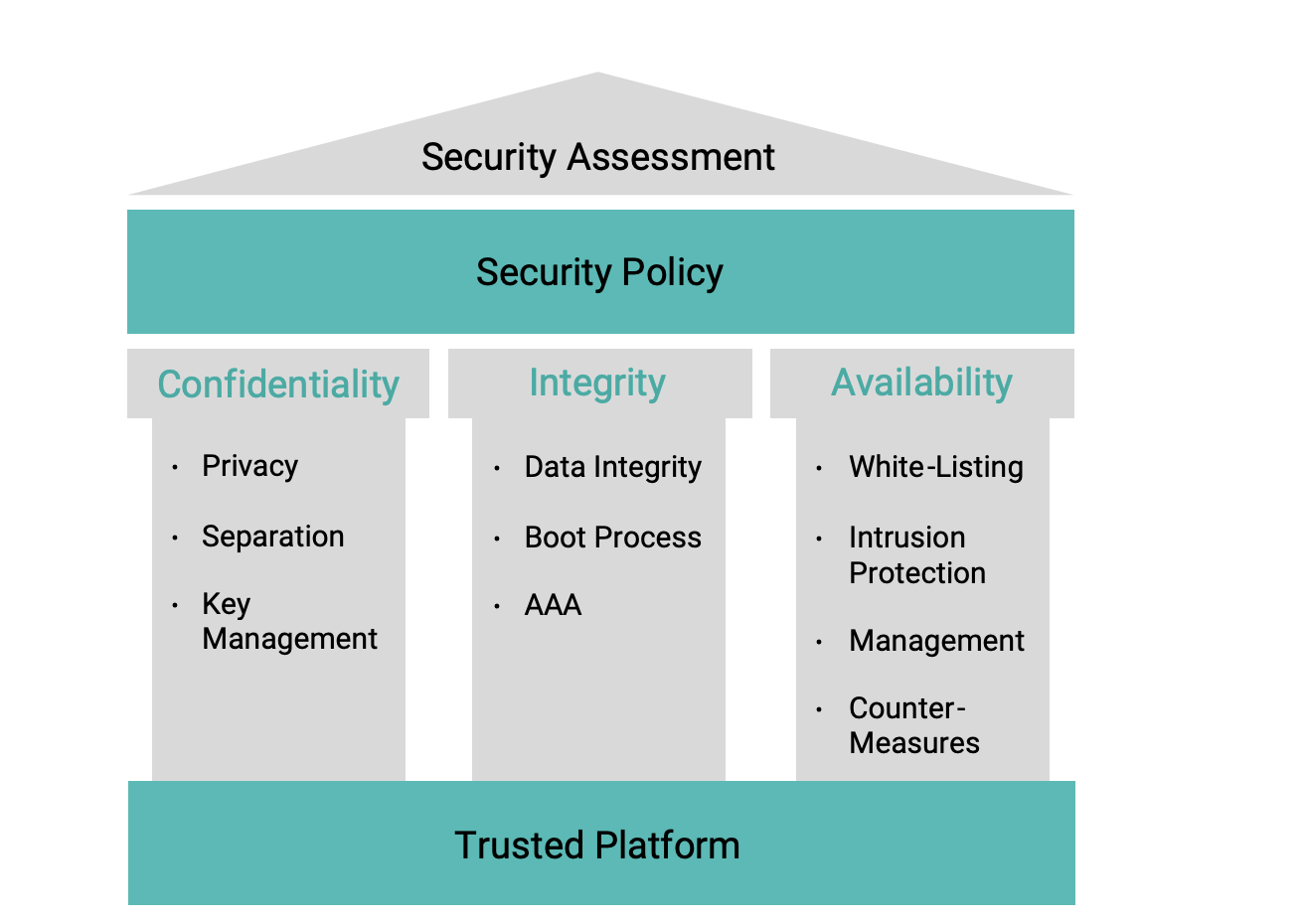
The NIST was founded in 1901 and is now part of the U.S. Department of Commerce. The NIST Framework for Improving Critical Infrastructure Cybersecurity is a set of industry standards and best practices to help organizations manage cybersecurity risk. In particular, the Framework defines the following five Core Functions, which are high-level steps to follow for implementing cybersecurity: Identify, Protect, Detect, Respond, and Recover.
- Identify: Cybersecurity begins with identification of the cybersecurity risk to healthcare systems, assets, data, and capabilities.
- Protect and Detect: Once the potential threats are identified, manufacturers can start development of specific device security measures to meet the expected threats.
- Respond and Recover: Using defense in depth and security techniques, devices in the healthcare system will be able to protect themselves against known attacks and detect attacks in real time. To be truly effective, however, medical device security needs to do more than just detect attacks; it needs to be able to respond quickly to detected attacks. High-level security policies will dictate the actions that need to be taken for each type of detected security event.
CYBERSECURITY STRATEGY
We now have the impetus to consider a cybersecurity strategy, with the regulatory framework flowing down from government and the growing awareness among medical device manufacturers of the high importance of implementing security into their products. This will minimize risk and also secure investments in new business models and next-generation cloud-based solutions.
Let’s start with the key stakeholders in the development and implementation of a successful security strategy, discuss their main pain points, and look at their goals.
These are:
- Medical device manufacturers: Those who design, build, deploy, and maintain medical devices
- Healthcare institutions: Hospitals and other healthcare establishments that use medical devices
- Regulatory bodies: Auditors from the FDA, Lloyd’s Register, TÜVs, and others
- Patients: Those whose conditions are monitored with revolutionary therapies and medication delivery and care beyond hospital walls
MEDICAL DEVICE MANUFACTURERS
Product managers, marketing managers, and service managers in the medical device industry have to make sure they build competitive devices that meet ever-changing regulatory requirements, especially around security. They must quickly find answers to these questions:
- How can we implement a security strategy that:
- Is clearly and effectively messaged to medical device manufacturers, their sales organization, and their customers?
- Meets both the end customer requirements (such as IEC 80001) and local security and disaster response laws (such as Katastrophenschutzgesetz in Germany or Federal Disaster Relief Act7 in the USA)?
- Supplies all of the correct documentation required by the regulatory authorities?
- Do we have trained staff who understand both safety and security requirements for medical devices?
- How do we support the IT manager of our customers in implementing an IEC 80001 strategy?
- Further, how do we respond to medical device equipment tenders that specify IEC 80001 and provide the necessary information for the end user to remain IEC 80001 compliant?
- How do we respond to the hospitals’ requirements, in terms of innovative methods of treatment, latest medical technology, cost-optimized services, or even completely new business models?
- Should we consider connected medical devices to support the drive toward smart hospitals? – How do we address the reservations of hospital operators?
- How do we enable data transfer to these systems, and do we retain data ownership and privacy?
- How do we maintain security when transferring data between these systems?