Enabling Embedded Solutions with Container Technology
Bring Portability, Security, and Manageability to Embedded Software Development and Distribution
Executive Summary

Monumental changes to embedded software development practices are underway to address the complexities of ongoing software lifecycle maintenance and critical security concerns. These challenges have captured the attention of many industry leaders who strive to enable and secure streamlined development and deployment methods.
Complementary technologies have spurred these changes. Such technologies have been driven by the growing adoption of edge computing, autonomous vehicles, medical devices for remote diagnosis and treatment, robotics, aerospace advances, and increasing 5G technology demands as mobile broadband and mmWave microcell installations proliferate.
Adopting cloud-native tools for development empowers teams to collaborate from around the world. Containers make this possible by sharing a common environment with reusable configurations for developing and deploying code. One of the advantages of using containers is that they can be adopted for both existing embedded applications and for new designs. Application developers, whether creating embedded or enterprise-focused programs, can deploy software written in Rust and Python using tools familiar to them. Think of it as a write-once, deploy-anywhere approach.
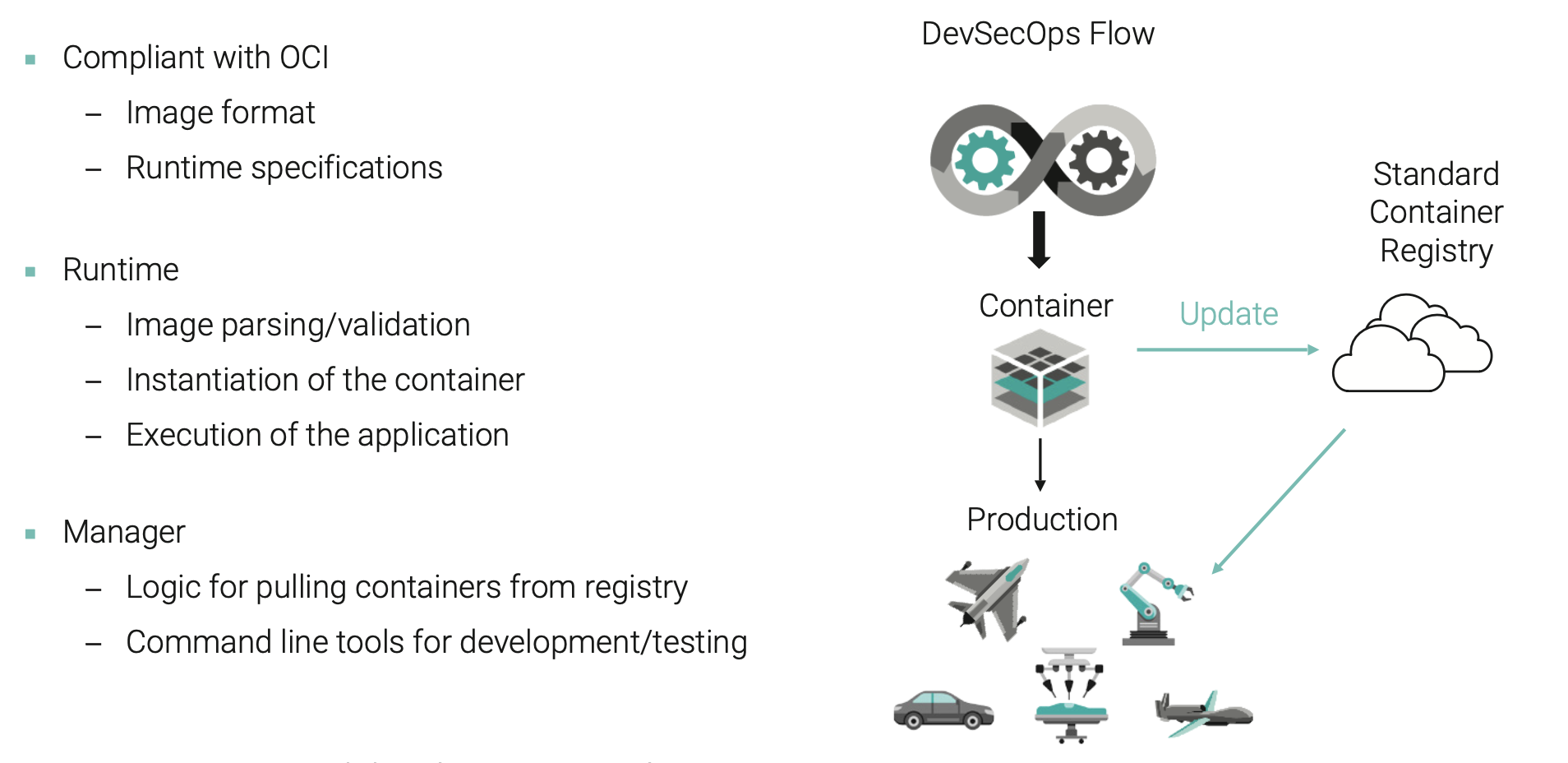
Real-time operating systems (RTOSes), VxWorks® in particular, are fundamental to embedded systems. The introduction of support for containers in VxWorks to systematically deliver and update software is transformational. Support for containers that can respond dynamically in a real-time, deterministic way to events in the environment is a critical and innovative element for creating a software-defined world. This is especially important for automated manufacturing lines, autonomous vehicle operation, aerospace applications, and medical devices, as digital transformation advances in these sectors.
Adoption has lagged to some degree due to a lack of awareness in the embedded industry of the benefits of container technology. Also, the consolidation of existing solutions around virtualization (virtual machines) implementation as standard has impeded adoption. Another impediment is concern over security issues related to a shared kernel causing a generalized breach among those applications connected to the same host. Finally, adoption has been hampered by a lack of skilled technicians and developers with the tools and expertise to implement container solutions for embedded use cases.
As discussed in this paper, these issues have been addressed in numerous ways, and the multiple benefits of containers enabling innovative embedded applications offer a promising future for the evolving software architecture that supports their creation and distribution.
Demystifying Container Technology


Where Are Containers Being Used in Different Markets?

Containers are ideally suited for applications in many vertical markets in which embedded software plays a significant role, including:
- Avionics: For commercial and military avionics companies looking to optimize space, weight, and power (SWaP), containerization is transformative. Being able to run applications in their own containers, independent of the underlying stack, enables greater portability and even reusability of legacy software packaged as containers deployed on a newer system. Examples of prime use cases are flight data analysis, flight management systems, 3D cockpit displays, user interfaces, in-flight entertainment systems, and aircraft system monitoring.
- Automotive: Automotive applications for container technology are among the most promising developments in the field, particularly as they support autonomous driving and software-defined vehicles. This new approach virtualizes vehicle equipment and consolidates various functions on a single hardware system. Due to modularity and compatibility, the concept of containers is used for updating and upgrading features over the air both faster and more securely. Containerized workloads can also support other use cases, such as in-vehicle infotainment, connected car services, real-time diagnostic alerts, predictive maintenance, fleet management, analytics, and telematics data.
- Industrial: Transformation is underway as Industry 4.0 changes are sweeping through markets. By running secure, isolated containers on single or distributed systems, industrial applications can be consolidated into fewer systems, improving scalability, simplifying deployment, and enhancing system update capabilities. It also ensures update-and upgrade-ready forward-looking architectures including predictive maintenance, AI-enabled robots and cobots, manufacturing-line automation, supply chain operations and logistics, augmented reality, virtual reality, and control systems.
- Telecommunications: Containers enable top service providers to deploy and securely update 5G and upcoming 6G networks. A world-leading telco equipment manufacturer is implementing initiatives using containers for 5G network slicing to support applications with differing performance requirements, such as augmented reality and virtual reality. 5G base stations equipped with mmWave capabilities use containers to distribute software in smart city environments and to ensure that current software patches are installed. Network utilities such as firewalls and load balancers can also be implemented through containers.
- Medical: In a highly regulated environment where device high availability is a matter of life and death, containerized workloads on underlying safety-certified operating systems enable critical environment separation of applications and data. Use cases enhanced through containers include remote patient care, health monitoring, imaging systems, infusion pumps, and surgical and robotic systems. These applications can utilize containers to deliver security patches and critical software updates. Surgical robots are being developed that are fully automated and can perform complete operations without human intervention.
As container technology matures, potential use cases are essentially unlimited.
Isolation of Applications Increases Security and Reliability

Containers isolate applications and their runtime operations for security, conflict avoidance, and management control. Common isolation techniques include the use of namespaces to control access to system resources and capabilities and to place limits on how much can be allocated. Containers sometimes use an overlay file system to share common files but keep any local changes private.
VxWorks has granular control over how its real-time processes (RTPs) can access kernel objects, view files and directories, and interact with kernel resources. By restricting access to system calls, applications can be isolated from each other and given a private sandbox to run in. The file system namespace provides a unique view of the file system to allow containerized applications to manage their libraries and configuration independently. Its overlay file system allows reduced footprint size through reuse of containers with a common base image without interfering with each other. The extensive network functionality in VxWorks — stemming from its history in telecommunications — also makes it possible to control the network interface provided to applications and the endpoints they can communicate with.
Containers provide additional hardening, particularly when features are combined with other security provisions. This can be valuable in embedded environments where container security is essential. For example, a secure boot technology establishes a chain of trust by validating the full range of software components, from the hardware root of trust through the bootloader and kernel, right down to the signed container and the application itself. Combining container security with secure boot provides an end-to-end chain of trust for software running on the device.
Integration of Mixed-Criticality Components
In some cases, containers deploy software developed with higher-level programming languages or open source software that cannot be certified. This results in containers with varying levels of criticality. Successful integration of these components, identifying certifications that have been met or compliance that has been granted, can help avoid the need to redo certain certification processes. To take full advantage of agile development practices and DevSecOps workflows, isolating components according to the level of criticality can retain the advantage of streamlined development while maintaining existing certifications for specialized components.
Embedded Deployment of Applications

Developing and Testing Containers with Wind River Simulation

Prospects for Container Technology


 —Nicolas Chaillan, founder, Ask Sage; former U.S. Air Force and Space Force Chief Software Officer
—Nicolas Chaillan, founder, Ask Sage; former U.S. Air Force and Space Force Chief Software Officer —Glen De Vos, Senior VP of Transformation and Special Projects, Aptiv
—Glen De Vos, Senior VP of Transformation and Special Projects, Aptiv