What Is
CVE Scanning?
Learn how to identify risks and mitigate threats so you can build higher-quality code and accelerate time-to-deployment.
What Is CVE Scanning?
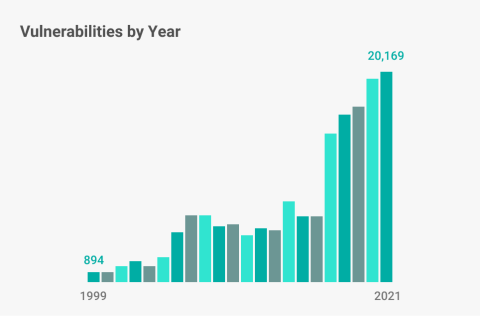
The CVE (Common Vulnerabilities and Exposures) database is a public list of reported security vulnerabilities. The fact that it is continually growing (see Figure 1) sets back efforts to manage and maintain a secure development environment. Monitoring the increasing number of exploits, which includes identifying, categorizing, and assessing their severity on your Linux platform, is critical — but it is also a complex and time-consuming task.
Of course, not every registered CVE will affect the version of Linux you use in a given RYO — but how can you be sure? You still must do an assessment on a staggering number of exposures just to find those that do affect your release. You might recall several exploits — Spectre and Meltdown in 2018 and WannaCry in 2017 — that made a dramatic splash in the public consciousness. They were illustrative of the types of vulnerability and ransomware challenges facing developers.
Vulnerability Management
Scanning code for CVEs and license compliance issues can help identify risks before they become liabilities. Critical and high-risk vulnerabilities impacting your code must be remediated. And, because new vulnerabilities are identified every day, ongoing CVE monitoring, prioritization, and mitigation is required.
This management involves several steps:
- Monitoring: Actively monitor security alerts from reliable external sources, customers, and any other external submitters.
- Assessment/prioritization: Assess and prioritize vulnerabilities based on severity, difficulty, and avoidability of the alert.
- Notification: Notify customers and submitter of the level of susceptibility within a short time target.
- Remediation: Post remediation action within a short time target, based on the classification of susceptibility.
10 CVE Scanner Must-Haves
As vulnerability reports have skyrocketed, two points have become clear: First, their frequency creates an endlessly moving target that many developers don’t have the resources to address, which exposes companies to significant business risk. Second, the nature of CVEs is not black and white, but many shades of gray.
There are 10 crucial elements of best-practice CVE scanning activities:
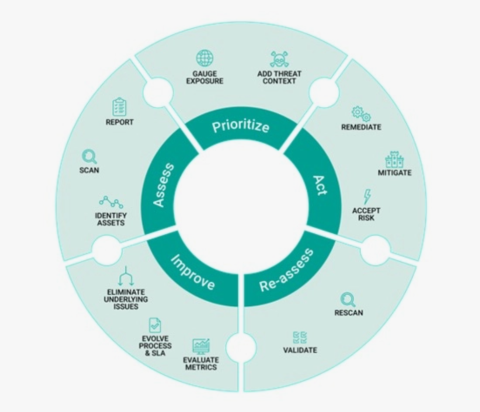
- Develop a vulnerability management lifecycle: Development teams need to manage vulnerability detection as a lifecycle (see Figure 2) that includes constant assessment, effective prioritization, scanning and detection, and a method for growing the library of known vulnerabilities so detection can improve over time. Scanning is never a one-and-done activity.
- Stay current: Vulnerability scanning is not enough. Staying up to date on changing CVEs is possible by using databases such as the CVE database provided by Wind River.
- Focus: Not all of today’s rapidly increasing threats are relevant for the embedded developer. A key step in effective vulnerability management is paring down the world of CVEs to a curated database of those vulnerabilities that have the most impact on embedded development teams.
- Use automated vulnerability identification: A structured approach that Wind River recommends is to take advantage of automation to help with vulnerability detection. Software bills of materials (SBOMs), which use the software package data exchange (SPDX) format, include not only descriptor information but also version, name, license, manufacturer, and other metadata associated with a given software package. Using this information, developers can create a powerful inventory of the software that comprises their Linux OS and/or application. This then becomes the foundation for intelligent vulnerability scanning that is tailored to the software in use.
- Triage efficiently: Initial scans can produce overwhelming results. The Common Vulnerabilities Scoring System (CVSS), however, provides a severity score for every CVE tracked. The Wind River vulnerability scanner can use this score to deliver a prioritized list of CVEs that have the highest impact on the code, helping developers zero in on the vulnerabilities that pose the greatest risk to their solutions.
- Use automated license and IP compliance identification: Running IP and license scans can be time-consuming if they are not automated. Fortunately, standardizing on a format such as SPDX for package descriptions and maintaining a disciplined SBOM enables developers to implement automated scans for license use and compliance.
- Integrate DevOps into development: By implementing automated vulnerability and CVE scanning early in the build process, developers become responsible for fixing known security risks early in the development phase. This, in turn, delivers benefits for the product lifecycle in general, including a higher security posture and a more agile model for responding to identified security issues. DevOps provides the needed shift-left tactic to achieve this strategy, which also drastically reduces time and cost.
- Use dashboards and health monitors: While search engines and vulnerability databases are helpful, development teams and engineering leadership need a consolidated, streamlined view of their platform and application status rather than having to hunt for and collect information from different sources. Dashboards provide a high-level view of status, must be understandable at a glance, and enable drill-down and detailed reporting where necessary. They should also be automatically updated to remain relevant and current at all times.
- Engage in reporting: Customers have an expectation that suppliers are validating their system components against known vulnerabilities, because those customers are in turn expected to prove that the devices they offer are secure. Development teams often find it necessary to invest in automation that shows CVE detection and resolution times. They may be also required to show the criticality of found CVEs, particularly for high-impact packages within the system.
- Ensure security and privacy: There are three characteristics to keep in mind when evaluating a secure solution for CVE scanning:
- Access control: The tool should provide strict access controls to prevent unauthorized access to sensitive information.
- Manifest protection: The tool provider must protect the assets that are being scanned for CVEs — usually source code and/or software packages. These manifests must be protected to ensure that your SBOM and other sensitive information about the components of the Linux platform or application don’t fall into the hands of bad actors.
- Customer privacy and protection: The tool should not compromise the relationship between the supplier and customer. This relationship should remain private thanks to various mechanisms, such as encryption, access controls, or other means of obfuscation.
Applying security safeguards is now a top priority for development teams. Still, these teams may not have the bandwidth or time to remediate security vulnerabilities, nor the experience of using proper compliance analysis tools.
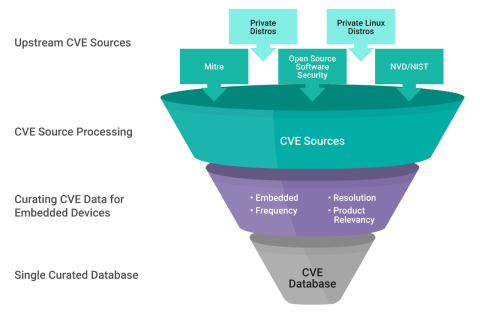
Leveraging automated security and compliance scanning tuned for complex embedded software systems can help developers quickly identify potential vulnerability or license issues in their solution. A professional-grade security and compliance scanner provides developers with a thorough assessment of the potential risks for common vulnerabilities and compliance issues. A vulnerabilities scanning assessment can help flag critical points of concern that require a deeper analysis to determine the impact and effort of mitigation, followed by an execution of a remediation plan to help close the technical debt identified. Wind River uses a curated collection of data sources, including the Yocto Project, NIST, and other public sources, and the Wind River Linux database to flag known common vulnerabilities and exposures.
How Can Wind River Help?
Wind River Studio Linux Services
SECURITY SCANNER
Wind River® offers a free, professional-grade Linux CVE scanner, specifically curated to meet the unique needs of embedded systems. Our security scanner uses your SBOM or manifests to identify critical CVEs. The results allow us to provide a deeper analysis to determine the impact and effort to mitigate.
We use a curated collection of data sources, including the Yocto Project, NIST, and other public sources, as well as the Wind River® database of CVEs.
We analyze specific platform layers, including hardware, kernel, user space, libraries, and other system components. All vulnerabilities are ranked according to the CVSS v3 scoring system and are presented in a graphical and easy-to-read format.
» Learn about our security scanner
SECURITY AND COMPLIANCE ANALYSIS AND REMEDIATION
You can also work with our Services team to perform a CVE scan and then quickly identify and prioritize vulnerabilities based on a common vulnerability threshold (the CVSS), severity of impact, and difficulty of attack and avoidance. We work with you to build release plans to address critical and prioritized CVEs by offering:
- A detailed security report identifying CVEs open against your platform
- Fixes for newly identified critical CVEs
- An online support portal for customers to request fixes for noncritical CVEs
- Requests for review by Wind River engineers, with timely responses
- Premium Support options for customers needing dedicated engineers well versed in their project
» Learn about our security analysis and remediation services
LIFECYCLE SECURITY
Wind River also offers ongoing CVE monitoring, mitigation, and management of your Linux platform throughout the software development and deployment lifecycle, with timely alerts to new CVEs as they emerge. Our team of engineers performs a deep analysis to determine the impact of each CVE on your Linux platform. We work with you to prioritize remediation options and timing. We backport, validate, and verify community-based patches before we apply them to your code. If a community solution is unavailable, we work with your engineering team to architect a technical solution.

